Programmable Key Pairs
Exploring the Mechanics, Use Cases, and Getting Started with PKPs
Introduction
Programmable Key Pairs (PKPs) represent an advancement in the domain of decentralized applications and blockchain technology. They provide a user-friendly and secure solution for interacting with Web3 applications, benefiting both developers and non-developers. In this beginner-friendly article, we will introduce you to the concept of PKPs and demonstrate how they can enhance your experience in the digital world.
By utilizing PKPs, individuals can effortlessly access Web3 applications without the burden of memorizing lengthy passphrases or juggling multiple accounts. This intuitive and convenient approach enhances the way users interact with blockchain-based platforms.
The true versatility of PKPs lies in their capability to function across diverse blockchains and state machines. Regardless of whether you are utilizing Ethereum, Cosmos, or any other blockchain network, PKPs enable secure transaction signing through the Elliptic Curve Digital Signature Algorithm (ECDSA). This signifies that you can engage in multiple blockchain ecosystems without the necessity of acquiring new authentication methods for each individual network.
PKPs offer a wide range of applications and use cases. They enable seed-phraseless onboarding experiences, automated transaction execution, and cross-chain messaging, thereby empowering both developers and non-developers to engage with the decentralized world in innovative and captivating ways.
In the upcoming sections of this article, we will delve into the resources, concepts, and practical examples that will enhance your understanding and effective utilization of PKPs. Whether you are a developer seeking to integrate PKPs into your applications or a non-developer in search of a user-friendly method to interact with Web3 platforms, this guide will equip you with the necessary knowledge to unlock the potential of Programmable Key Pairs. Let us embark on this exhilarating journey together!
Overview:
What are Programmable Key Pairs?
A programmable key pair refers to a specific type of key pair that has the capability to be programmed to carry out specific tasks. This makes programmable key pairs highly versatile, enabling their utilization in a wide range of applications.
In the context of blockchain technology and smart contracts, programmable key pairs operate as a distinctive set of keys that possess the ability to control and automate actions within a digital system. They act as specialized keys that grant authority over specific functionalities and operations within the system, allowing for efficient and secure automation of various processes. They are also special key pairs that can be used within smart contracts to control access and trigger actions, a programmable key pair could be programmed to sign documents, encrypt files, or generate random numbers.
To illustrate the practical application of programmable key pairs, let's consider a scenario where you possess an NFT, and you aim to sell it securely. By leveraging programmable key pairs, you can create a smart contract that stipulates that the art piece can only be transferred to a new owner if the buyer provides the correct programmable key pair. The smart contract acts as a self-executing agreement that automatically verifies whether the provided key pair matches the specified conditions. If the conditions are met, the smart contract proceeds with the transfer of ownership.
In this manner, programmable key pairs empower you to establish rules and conditions within smart contracts, facilitating secure and automated actions within a blockchain system. By utilizing programmable key pairs, you can enhance the trustworthiness, transparency, and efficiency of digital asset transactions.
Consider another scenario where you possess a sizable sheet of paper adorned with numerous dots. Each dot represents data, and the arrangement of these dots conceals a confidential message. Your objective is to share this message with a friend while ensuring its secrecy from prying eyes that are not your friends.
To achieve this, you could divide the paper into multiple fragments, with each fragment containing a portion of the secret message. Subsequently, you would distribute these individual paper fragments to different friends. The retrieval of the secret message would necessitate the collaboration of your friends, as they would need to assemble all the fragments back together.
Programmable Key Pairs (PKPs) operate on a similar principle. In this analogy, the private key of the PKP represents the secret message, while the shares of the private key serve as fragmented pieces of paper. Each individual share of the private key is held by a particular node within the network.
To carry out a transaction signing process, consensus is required among the majority of nodes in the network. They combine their respective shares of the private key to generate the complete signature. This approach enhances the security of PKPs significantly, as even if an attacker manages to compromise one or more nodes, they would be unable to steal the private key or execute unauthorized transactions.
Indeed, the explanation can be summarized as follows:
A Programmable Key Pair (PKP) is a cryptographic key pair that is collectively generated by a network of nodes.
The private key of the PKP is distributed among the nodes, with each node storing only a share of the private key.
To sign a transaction using PKP, consensus is required among the majority of nodes in the network. They combine their individual shares of the private key to create the complete signature.
This distributed nature of PKPs enhances their security, as even if an attacker gains control over one or more nodes, they would not be able to obtain the full private key or authorize unauthorized transactions.
Why are Programmable Key Pairs important?
Enhanced Security: PKPs offer an elevated level of security in comparison to traditional authentication approaches, employing cryptographic methods to safeguard valuable data and guarantee that only authorized individuals can gain access to and engage with digital assets or systems. The enhanced security of PKPs arises from the fact that the complete private key is never stored on a single node, rendering it significantly more challenging for attackers to pilfer it.
Decentralization and Trust: In decentralized systems, PKPs have a crucial function as they eliminate the necessity for central authorities or intermediaries. By enabling direct peer-to-peer interactions, PKPs promote trust and transparency. They play a significant role in building decentralized networks and applications, where control is distributed among participants rather than being concentrated in a single entity.
Versatility: PKPs can be programmed to perform a variety of tasks, making them more versatile than traditional key pairs. For example, a PKP could be used to sign documents, encrypt files, or generate random numbers.
Fault tolerance: PKPs are fault-tolerant, meaning that they can continue to function even if one or more nodes in the network fail. This is important for applications that require high availability, such as financial transactions and secure communication.
What are the benefits of using Programmable Key pairs?
PKPs are designed to be compatible with a wide range of blockchain networks and decentralized applications. They possess the capability to function effectively across diverse platforms and protocols, facilitating smooth integration and interoperability. This flexibility empowers users to conveniently access and manage their digital assets across multiple systems by utilizing a single PKP.
PKPs are programmable, meaning they can be customized and adapted to meet specific requirements. Developers can define rules and conditions associated with PKPs, empowering them to create applications with logic and automation capabilities.
PKPs provide a user-friendly experience by simplifying processes such as onboarding and authentication. They eliminate the need for complex procedures like remembering and managing seed phrases or passwords, making it easier for users to interact with decentralized applications. PKPs can help increase user adoption of Web3 by making it easier and more secure to use.
PKPs enable trustless transactions, where participants can engage in secure interactions without relying on a central authority.
PKPs improve efficiency by automating tasks and reducing the need for manual intervention.
PKPs can help enhance security by making it more difficult for attackers to steal or compromise private keys.
Uses cases of Programmable Key pairs:
Here are six (6) examples of use cases for Programmable Key Pairs:
Multi-signature wallets: PKPs can be used to create multi-signature wallets, which require multiple signatures to authorize a transaction. This can be useful for organizations that want to secure their funds or for individuals who want to share control of their wallets with others.
Content distribution: PKPs can be used to distribute content in a secure and decentralized way. This can be done by using PKPs to sign and encrypt content, and to track the distribution of content.
Cross-chain transactions: PKPs can be used to facilitate cross-chain transactions, which are transactions that are executed across multiple blockchains. This can be done by using PKPs to sign transactions and to verify the authenticity of transactions.
Verifiable credentials: PKPs can be used to create verifiable credentials, which are digital certificates that can be used to prove an identity or attribute. This can be useful for applications such as self-sovereign identity and decentralized finance.
Decentralized applications (dApps): PKPs can be used to secure dApps, which are applications that run on a decentralized network. This can be done by using PKPs to sign transactions and to authenticate users.
Conditional transactions: PKPs can be used to create conditional transactions, which can only be executed if certain conditions are met. This can be used to implement features such as fraud prevention and compliance checks.
These are just a few of the many use cases for Programmable Key Pairs. As the technology continues to develop, we can expect to see even more innovative use cases for PKPs in the future.
Quick Start Guide for Developers:
Now that we understand what Programmable Key pairs are all about. The next step is to learn how to integrate Programmable Key pairs (PKPs) into our applications using Lit Protocol, To proceed, please follow the following quick start guide:
What is Lit Protocol?

According to Lit Protocol definition, Lit Protocol has distributed cryptography for encryption, computation, and programmable signing. As a generalizable key management layer, Lit provides developers with a comprehensive toolkit for managing sovereign identities on the open Web.
Here is a brief explanation of the two main services that Lit Protocol provides:
Encryption: Lit Protocol can be used to encrypt data so that it can only be decrypted by authorized users. This can be used to protect sensitive data, such as financial information or medical records.
Programmable signing: Lit Protocol can be used to create programs that can sign data on behalf of users. This makes it possible to automate tasks and improve efficiency.
Here are some of the benefits of using Lit Protocol:
Security: Lit Protocol uses threshold cryptography to secure its keys, making it very difficult for an attacker to compromise them.
Interoperability: Lit Protocol is blockchain-agnostic, which means that it can be used with any blockchain or other distributed ledger technology.
Programmable: Lit Protocol can be used to create programs that can sign data on behalf of users. This makes it possible to automate tasks and improve efficiency.
Scalability: Lit Protocol is a distributed network, which means that it can scale to meet the needs of even the most demanding applications.
To test and setup lit protocol programming key pair, you have to follow the steps below:
Visit Lit Exprolore. To ensure comprehension among developers and non-developers, we will utilize Lit Explorer for setting up and explaining the fundamental concepts and workings of PKPS in this tutorial.

Connect Wallet: In order to utilize lit explorer, the necessary step is to establish a connection to the website, which automatically adds the Chronicle Lit Protocol Testnet Network.
Mint a Programmable Key Pair (PKP):
After successfully uploading our code to IPFS, the next step is to create a PKP (Protocol Key Pair). However, to mint the PKP successfully, we require access to the Chronicle-Lit Protocol Testnet.
When you visit the website, paste your address into the designated field, complete the verification process to confirm you're not a robot, and then click on the "CLAIM" button. If the process is successful, you will see the transaction hash displayed below.

The next step is to mint a PKP:
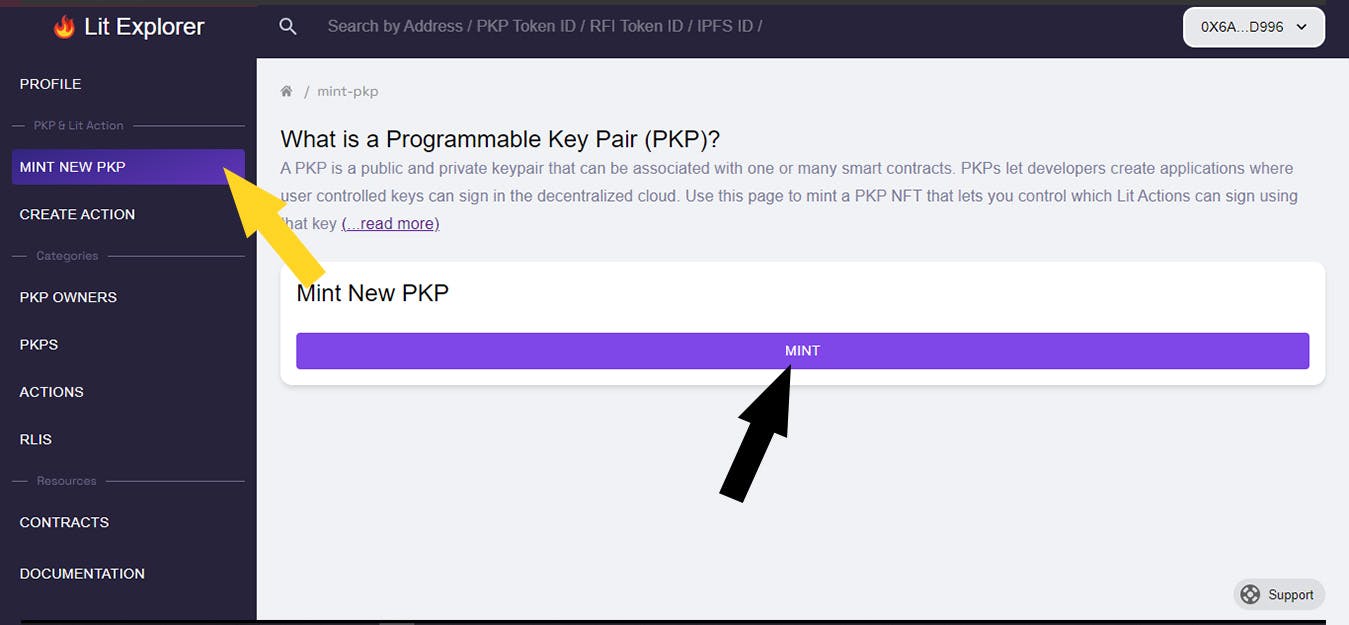
After clicking the "Mint" button, a Metamask window will appear, prompting you to approve the transaction.
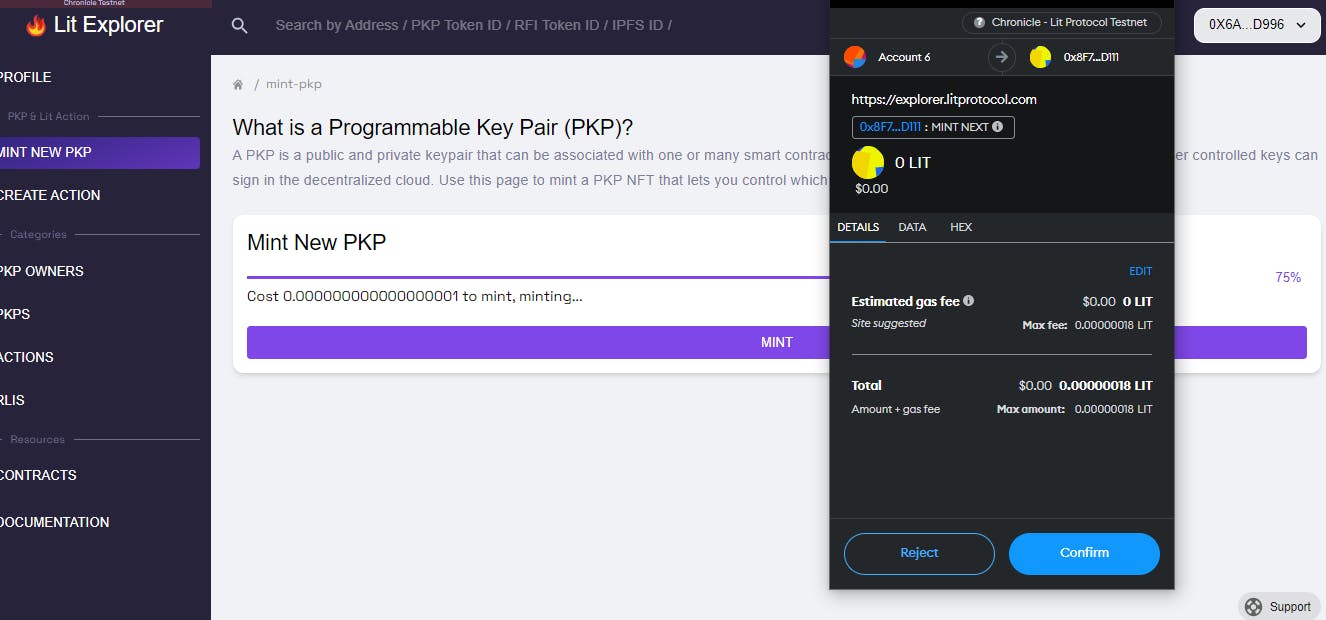
Once you have approved the transaction, you will receive a notification indicating that the transaction was successful.

Create a Lit Action: Lit Actions refer to JavaScript functions that make use of the threshold cryptography capabilities provided by Lit Protocol. These functions enable various actions and operations within Lit Protocol ecosystem, allowing users to leverage the power of threshold cryptography for enhanced security and privacy.
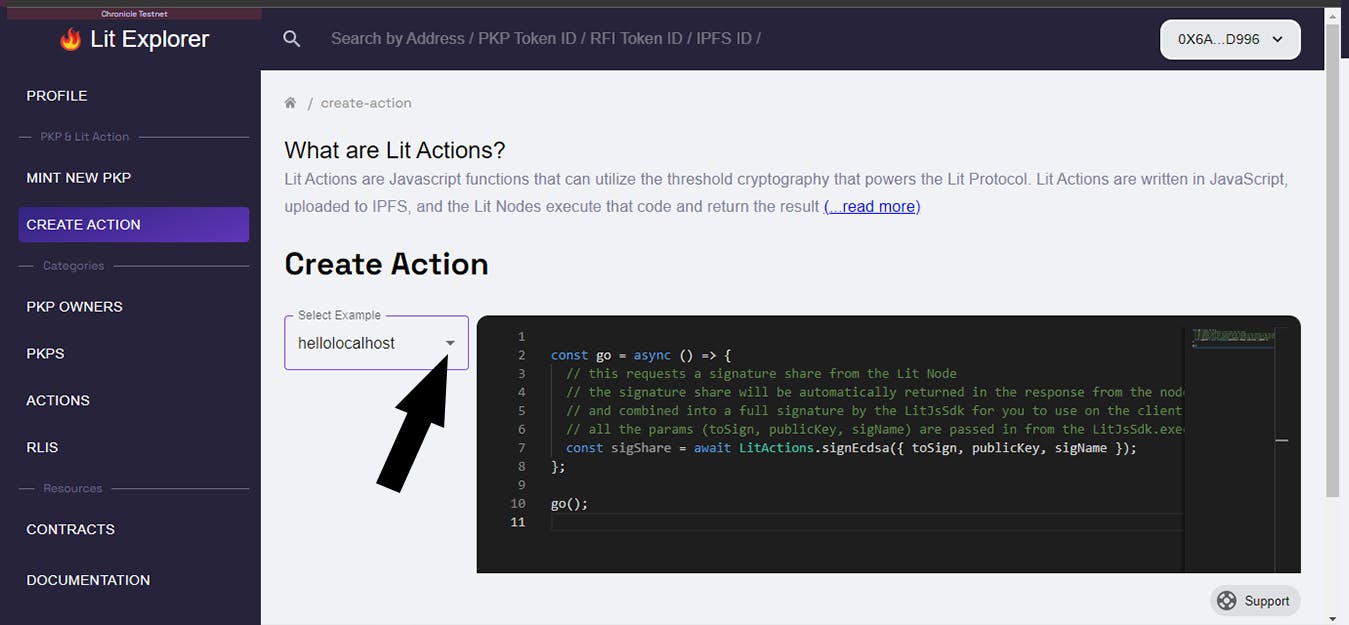
Click on the dropdown menu and choose the option labeled "lit conditions" from the available choices in the dropdown list.
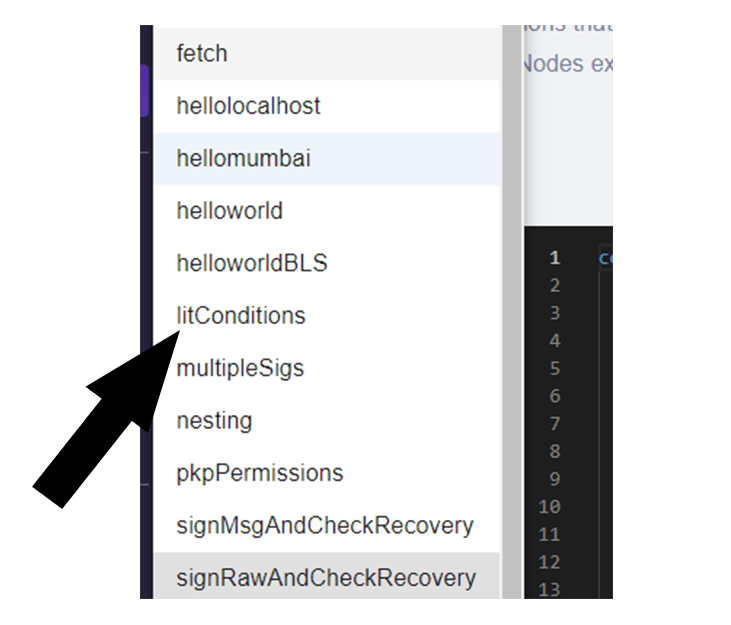
Once you have selected litConditions option, the following code will be displayed. To better comprehend the functionality of this code, let's analyze it step by step.
// This function tests an access control condition and signs a message if the condition is true.
const go = async () => {
// The `LitActions` object is a JavaScript library that provides access to the Lit Node.
const LitActions = require('lit-actions');
// The `checkConditions` function tests an access control condition.
// The condition is defined by the `conditions` object.
// The `authSig` object is the signature of the access control condition.
// The `chain` object is the chain ID of the blockchain that the condition is defined on.
const testResult = await LitActions.checkConditions({
conditions: {
// This is the access control condition.
// In this case, the condition is that the user has the public key "1".
pubKey: "1"
},
authSig: "signature",
chain: "chain-id"
});
// This line logs the result of the checkConditions function to the console.
console.log('testResult', testResult);
// If the testResult is false, the function returns without signing the message.
if (!testResult){
return;
}
// This is the string "Hello World" for testing.
// The `toSign` object is a string of bytes representing the string "Hello World".
const toSign = [72, 101, 108, 108, 111, 32, 87, 111, 114, 108, 100];
// This requests a signature share from the Lit Node.
// The signature share will be automatically returned in the HTTP response from the node.
const sigShare = await LitActions.signEcdsa({
toSign,
publicKey: "1",
sigName: "sig1"
});
};
go();
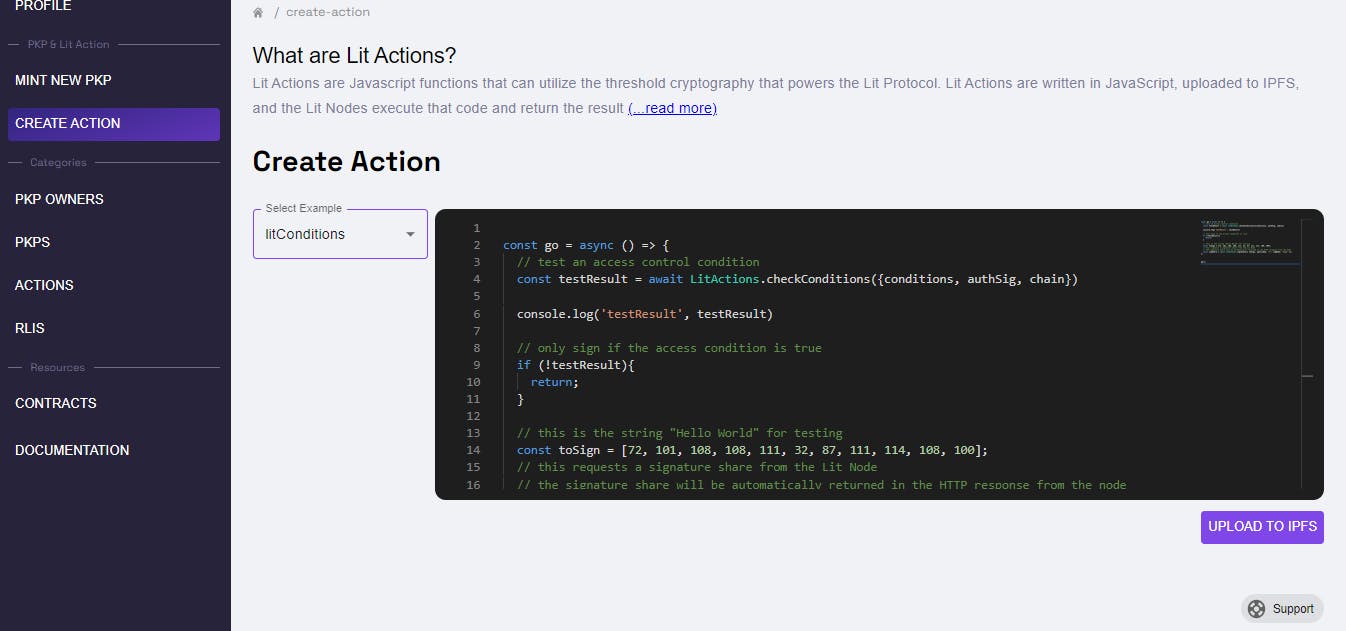
Proceed to select the UPLOAD TO IPFS button in order to generate a decentralized record of the code. This record will grant the Lit network permission to execute the code using your key pair. Upon successful completion of the upload process, you will receive the aforementioned message.
Authorize PKP Controllers:

Suppose this project was intended for a team project, and you wish to grant a team member permission to access and control a specific PKP. The initial action involves visiting the profile and selecting the PKP Token ID, which will lead us to the subsequent page mentioned below.
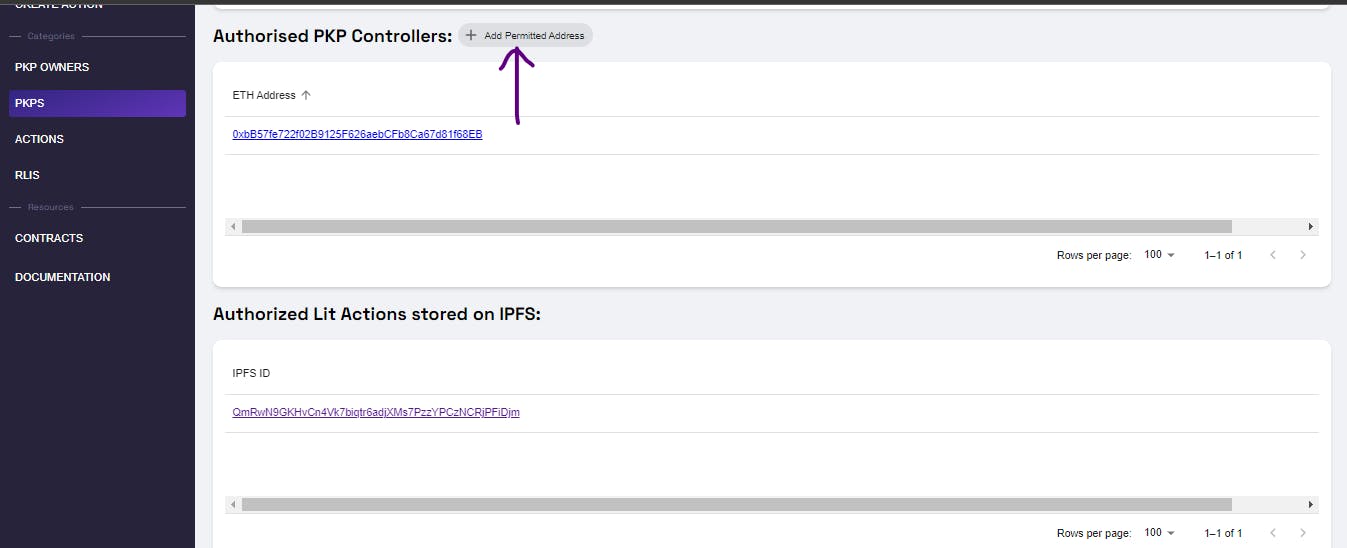
Click Add Permitted Address.
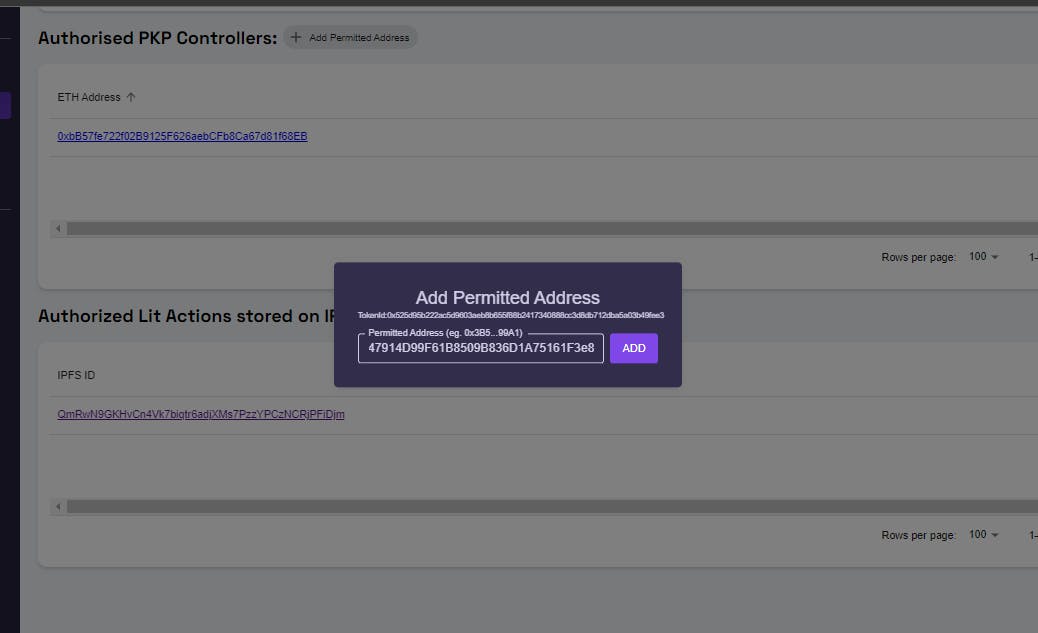
Enter/paste the address in the provided input box and click the Add button. This will trigger a metamask transaction to appear, where you should confirm the transaction and wait until it is successfully processed.
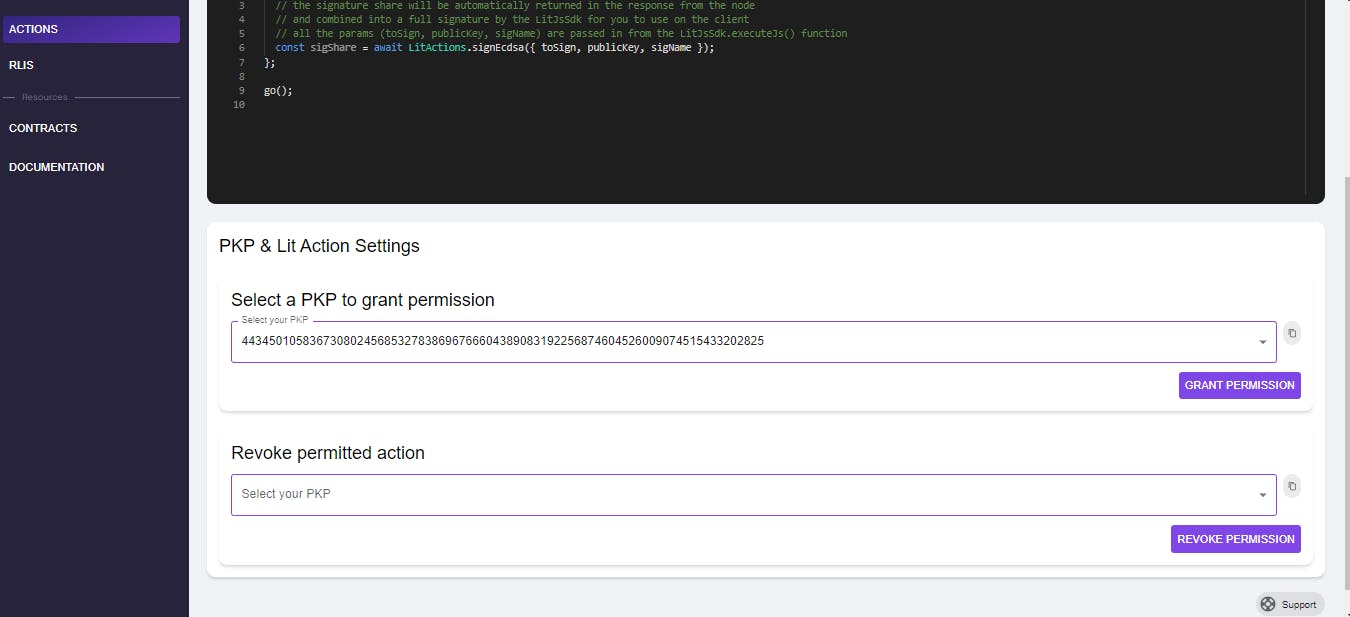
- Assign a PKP to Lit Action:

Click the IPFS ID and designate a PKP for authorization. This implies the creation of a fresh PKP and allowing a Lit Action to possess the ability to sign using it.
Conclusion
In conclusion, Programmable Key Pairs (PKPs) and Lit Protocol offer numerous benefits and opportunities for both developers and non-developers in the decentralized world. PKPs provide enhanced security, decentralization, and versatility, making them a powerful tool for interacting with blockchain networks and decentralized applications.
The programmability of PKPs empowers developers to create custom logic and automate actions within their applications, resulting in unique and innovative user experiences. PKPs enable multi-signature wallets, conditional transactions, verifiable credentials, decentralized applications, content distribution, and cross-chain transactions, among other use cases.
By using PKPs and embracing Lit Protocol, individuals, and organizations can enjoy improved security, efficiency, and trustless transactions. PKPs offer scalability, fault tolerance, and interoperability, enabling the creation of robust and future-proof applications.
It is crucial for users to start utilizing Lit Protocol and PKPs in their interactions with the decentralized world. By doing so, they can enhance their security, streamline their processes, and unlock the full potential of blockchain technology.
Start your journey with PKPs and Lit Protocol today and experience the benefits of a more secure, decentralized, and versatile digital landscape. Together, we can shape the future of programmable interactions and unlock the true potential of Web3 applications.
Reference Links:
